Organizing for the implementation of the Privacy Protection Law (Databases)
We would like to inform you that recently there has been a significant development in the field of enforcement of the Privacy Protection Law. Regarding databases It should be emphasized that failure to comply with the regulations under the law constitutes a criminal offense.
We will remind you that in March 2017, the Knesset approved the Privacy Protection (Information Security) Regulations, which detail the manner
The application of the information security obligation, imposed by the Privacy Protection Law, on any entity that manages or processes a database of
Personal information (the regulations entered into force in May 2018)
required according to the regulations
The regulations detail steps for managing and implementing information security, in accordance with the sensitivity of the databases and information
found in them, according to 4 levels of security that the regulations define:

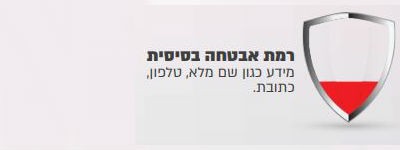
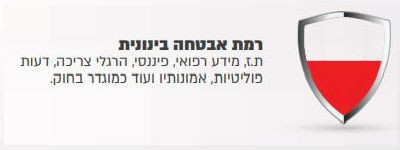

According to the level of information security, the regulations require implementation in several subjects, for example:
Writing an information security procedure
Physical controls to protect the information (for example cameras / access control)
Strengthening information security in the personnel recruitment process
Response procedure for information security incidents
For information security events mapping computer systems related to databases
Information security management
How do you organize?
The organization begins with the discovery of all the databases that contain information defined by law as requiring security, some of them are self-evident, some less so, for example an Excel file containing certain personal details about interested parties - may be considered a database.
After mapping the databases, the level of information security in the databases is actually tested and based on the results, the necessary route to protect them to the right extent within the law is built.
Phase I - mapping and review of gaps
Mapping the databases that exist in the kibbutz (such as community, employees, suppliers, customers).
Determining the level of information security (single authority, basic, medium, high).
Gap survey (the gaps that exist versus what is required to be carried out in the regulations).
Phase B - Implementation of the requirements of the regulations and reduction of gaps
Implementing the completion of the gaps in favor of compliance with privacy protection regulations.
Preparation of a folder for management and presentation in the event of an audit by the Authority for the Protection of Privacy.
for further details:

You may be interested in:

החשיבות של סריקות פגיעויות באבטחת סייבר

הכוח של ניטור הרשת האפלה באבטחת מידע

התיקון ה-13 לחוק הגנת הפרטיות

אבטחת מידע בענן

הרמת כוסית ראש השנה 2024






